In the modern digital age, video conferencing has become an essential part of the corporate, educational, and social world. Among the various video conferencing tools available, Zoom has become one of the most popular platforms for virtual meetings. But with the rise in usage, there is a corresponding rise in the threats, and one of the most dangerous security threats is Zoom bombing. This article will explore the idea of Zoom bombing in detail.
What is Zoom Bombing?
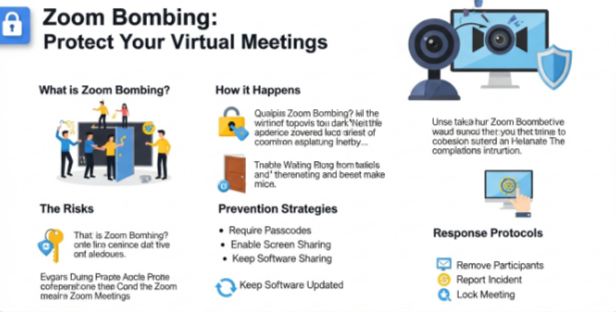
Zoom bombing is the term used to describe the unwanted entry of a person or group of people into a Zoom meeting, which can be done with the intention of causing disruption, harassment, or chaos. The unwanted participants, known as “Zoom bombers,” can display inappropriate material, flood chat boxes with spam messages, or even gain control of meeting functionality if the right safeguards are not in place.
The problem has increased dramatically during the COVID-19 pandemic, when millions of people turned to online meetings and online classes. Hackers and pranksters took advantage of the low security settings on online meetings that lacked any form of access control.
Keywords: Zoom bombing, Zoom bombers, virtual meeting disruption, Zoom security risks
How Zoom Bombing Happens
Understanding the mechanics of Zoom bombing is essential for prevention. Here are the most common ways attackers gain access:
-
Public Meeting Links
Sharing Zoom meeting links publicly on social media or unsecured platforms allows anyone with the link to join. Zoom bombers often scour such links for opportunities. -
Weak Passwords or No Password
Meetings without passwords or using simple, easily guessable passwords are prime targets. -
Screen Name Exploits
Some attackers use deceptive screen names to bypass participant recognition. For instance, they may pose as “Host” or “Teacher.” -
Unsecured Meeting Settings
Features like “Join before host,” screen sharing enabled for all participants, and open chat rooms can all be exploited by malicious actors. -
Phishing and Malware Attacks
Advanced Zoom bombers may employ phishing attacks to trick users into granting access or installing malicious software.
Keywords: Zoom security, Zoom vulnerabilities, unauthorized Zoom access, phishing Zoom attacks
Types of Zoom Bombing
Zoom bombing can manifest in various forms, depending on the attacker’s intent. Common types include:
1. Disruptive Attacks
These attackers aim to interrupt meetings with loud noises, inappropriate images, or offensive language. This type is most common in school classrooms or public webinars.
2. Harassment
Some Zoom bombers target specific individuals or groups, often sharing threatening or harassing messages. Workplace meetings and online classes are frequent targets.
3. Data Theft
In more sophisticated attacks, Zoom bombers may attempt to gain access to sensitive information, including meeting recordings, confidential presentations, or login credentials.
4. Spamming
Massively disruptive spam attacks flood chat boxes or use emojis, memes, or repeated text to create chaos in meetings.
Keywords: Zoom meeting disruption, online harassment, Zoom data theft, Zoom spam attacksThe Risks of Zoom Bombing
Zoom bombing poses several serious risks to users and organizations:
-
zoom bombing : Loss of Privacy
Attackers may access private discussions, sensitive documents, and personal information. -
Emotional and Psychological Impact
Victims, especially students and employees, can experience stress, anxiety, or embarrassment. -
Professional Reputation Damage
Companies hosting Zoom sessions for clients or public events may suffer reputational harm due to unprofessional disruptions. -
Legal Implications
Organizations may face legal consequences if confidential or personal information is compromised during a Zoom bombing attack. -
Financial Loss
In severe cases, Zoom bombers may attempt ransomware attacks or extortion through meeting disruption.
Keywords: Zoom bombing consequences, Zoom meeting privacy, emotional impact Zoom bombing, financial risks online meetings
How to Prevent Zoom Bombing
Preventing Zoom bombing requires proactive measures. Here’s a comprehensive list of strategies:
1. Use Meeting Passwords
Always set strong, unique passwords for every Zoom session. Avoid using easily guessable codes like “123456.”
2. Enable Waiting Rooms
The waiting room feature allows hosts to manually admit participants, giving complete control over who joins the meeting.
3. Limit Screen Sharing
Set screen sharing to “Host Only” by default. Allow participants to share only when necessary and monitor their actions.
4. Update Zoom Regularly
Zoom frequently releases security updates. Keeping the app updated ensures the latest protections against intrusions.
5. zoom bombing: Avoid Public Sharing of Links
Share meeting links through secure channels like email or messaging apps. Avoid posting links publicly on social media.
6. Lock the Meeting
Once all participants have joined, consider locking the meeting to prevent late arrivals or unauthorized access.
7. Monitor Participant Behavior
Assign a co-host to monitor participants’ names, activity, and any suspicious behavior.
8. Disable File Transfer
Disable file transfer during meetings to prevent malicious files from being shared.
9. Educate Participants
Educate team members, students, and colleagues about Zoom security practices. Awareness significantly reduces the likelihood of attacks.
Keywords: Zoom security tips, prevent Zoom bombing, secure Zoom meetings, Zoom privacy best practices
What to Do if Your Meeting is Zoom Bombed
Despite precautions, incidents may still occur. Here’s how to handle a Zoom bombing attack:
-
Remove the Intruder
Immediately identify and remove the offending participant(s) from the meeting. -
Report to Zoom
Use Zoom’s report feature to notify them of abusive behavior or security breaches. -
Lock the Meeting
If feasible, lock the meeting to prevent further intrusions. -
Mute or Disable Video for All
Muting participants and disabling video can quickly control disruptive behavior. -
Record Evidence
Document the incident with screenshots or recordings if needed for reporting or investigation. -
Communicate With Attendees
Reassure participants and provide guidance on preventing future disruptions. -
Review Security Settings
Post-incident, review and adjust all Zoom security settings to prevent recurrence.
Keywords: Zoom boming response, remove intruders Zoom, report Zoom abuse, Zoom emergency measures
Advanced Zoom Security Features
For organizations seeking higher security, Zoom offers advanced tools:
-
Single Sign-On (SSO)
Requiring SSO ensures that only authorized users from your organization can join meetings. -
End-to-End Encryption
Zoom’s E2EE prevents unauthorized access to meeting content, even if someone intercepts the connection. -
Role-Based Access Control
Assign host, co-host, and participant roles carefully to limit access to sensitive controls. -
Analytics and Audit Logs
Monitoring meeting logs can help identify suspicious activity patterns and prevent repeat incidents. -
Two-Factor Authentication (2FA)
Requiring 2FA adds another layer of protection against account compromise.
Keywords: Zoom E2EE, Zoom SSO, Zoom role-based security, Zoom 2FA, secure virtual meetings
The Future of Zoom Security
With the increasing popularity of remote work and online education, Zoom and other such platforms are working on security innovations. AI-powered monitoring, spam filtering, and advanced encryption are expected to become common features. Users need to be aware of the latest security measures to ensure secure online interactions.
Conclusion : zoom bombing
Zoom bombing is a serious issue in the modern digital age. Zoom bombing can interfere with meetings, invade privacy, and have a negative effect on the individuals involved. But by understanding how it happens, taking steps to prevent it, and being prepared to deal with it when it does occur, you can ensure that your virtual space is a safe and productive one.
Whether you are teaching a class, conducting a business meeting, or hosting a webinar, Zoom security is a priority. The key to preventing Zoom bombing is to be prepared.
FAQs About Zoom Bombing
Q1: Can Zoom bombing be completely prevented?
While no system is entirely foolproof, proper security measures drastically reduce the risk.
Q2: Is Zoom bombing illegal?
Yes, unauthorized access to digital meetings can be considered cyber harassment or trespassing under certain laws.
Q3: Can Zoom bombing happen on free accounts?
Yes, free Zoom accounts are often targeted because they may lack advanced security features.
Q4: How do I educate participants about Zoom bombing?
Host short training sessions or send guidelines on safe Zoom practices, including password protection and responsible sharing.
Q5: What should schools do to prevent Zoom bombing?
Schools should enforce strict access controls, enable waiting rooms, and monitor participant activity during virtual classes.